IoT-Based Smart Lock with Real-Time Person Detection Using YOLOv5 and Mobile App Integration
DOI:
https://doi.org/10.51252/rcsi.v5i2.1005Keywords:
Computer vision, IoT security, mobile application, person detection, smart lockAbstract
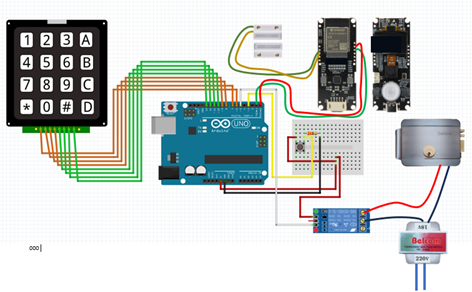
This article presents the design and implementation of a smart electronic lock system that integrates Internet of Things (IoT) technologies, computer vision, and multifactor authentication to enhance residential security. The solution is built upon a LilyGo ESP32-S3 microcontroller with an embedded camera and leverages a YOLOv5-based person detection model for real-time monitoring. A mobile application, developed in Flutter and integrated with Firebase, enables secure user interaction, remote access control, and real-time alerts. The system combines three authentication factors: a keypad code, visual detection of authorized individuals, and mobile app verification. Experimental validation with ten participants demonstrated an average detection accuracy of 96%, outperforming comparable systems. The proposed approach stands out for its low cost, modularity, and high adaptability to smart home environments. This research contributes to the development of accessible and robust security solutions using edge AI and distributed architectures.
Downloads
References
Aggarwal, S., & Sharma, S. (2022). Voice Based Secured Smart Lock Design for Internet of Medical Things: An Artificial Intelligence Approach. 2022 International Conference on Wireless Communications Signal Processing and Networking (WiSPNET), 1–7. https://doi.org/10.1109/WiSPNET54241.2022.9767113
Alves de Abreu, B., Paim, G., Alrahis, L., Flores, P., Sinanoglu, O., Bampi, S., & Amrouch, H. (2025). On the Efficacy and Vulnerabilities of Logic Locking in Tree-Based Machine Learning. IEEE Transactions on Circuits and Systems I: Regular Papers, 72(1), 180–191. https://doi.org/10.1109/TCSI.2024.3457541
Amaya Fariño, L., Tumbaco Reyes, A., Roca Quirumbay, E., Villón González, T., Mendoza Morán, B., & Reyes Quimís, Á. (2020). El IoT aplicado a la Domótica. Revista Científica y Tecnológica UPSE, 7(1), 21–28. https://doi.org/10.26423/rctu.v7i1.490
Castaño-Gómez, M., López Echeverry, A. M., & Villa Sánchez, P. A. (2022). Revisión del uso de tecnologías y dispositivos IoT en los sistemas de seguridad física. Ingeniería y Competitividad, 24(1). https://doi.org/10.25100/iyc.v24i1.11034
Chandrappa, S., Prithviraj, H, A. P., I S, R., R, M. S. K., & R, S. S. (2025). Smart Locker 2.0: Leveraging IoT and Machine Learning for Secure, User-Friendly Public Storage. 2025 International Conference on Artificial Intelligence and Data Engineering (AIDE), 696–700. https://doi.org/10.1109/AIDE64228.2025.10987522
Chowdhury Joy, M. H., Karim, M. M. A., Choudhury, A. H., Razin, M., & Ahmed, S. N. M. (2023). An IoT Based Smart Vault Security and Monitoring System with Zero UI. 2023 3rd International Conference on Robotics, Electrical and Signal Processing Techniques (ICREST), 95–100. https://doi.org/10.1109/ICREST57604.2023.10070057
Derbali, M. (2025). Facial authentication based smart door lock system and anomaly detection using machine learning architectures integrated with IoT. Research Square Preprint. https://doi.org/10.21203/rs.3.rs-3247506/v1
Hashim, K., Qasim, H., Hamzah, A., Hasan, O., & Al-Jadiri, M. (2023). Door lock system based on internet of things and Bluetooth by using Raspberry Pi. Bulletin of Electrical Engineering and Informatics, 12(5), 2753–2762. https://doi.org/10.11591/eei.v12i5.5134
Ibrahim, S., Shukla, V. K., & Bathla, R. (2020). Security Enhancement in Smart Home Management Through Multimodal Biometric and Passcode. 2020 International Conference on Intelligent Engineering and Management (ICIEM), 420–424. https://doi.org/10.1109/ICIEM48762.2020.9160331
Kar, A., Chauhan, Y. S., & Amrouch, H. (2024). Innovations in Hardware Security: Leveraging FeFET Technology for Future Opportunities. 2024 IEEE Asia Pacific Conference on Circuits and Systems (APCCAS), 457–460. https://doi.org/10.1109/APCCAS62602.2024.10808824
Karimi, K., Kabrane, M., Hassan, O., & Krit, S. (2020). Secure Smart Door Lock System based on Arduino and Smartphone App. Journal of Advanced Research in Dynamical and Control Systems, 12(1), 407–414. https://doi.org/10.5373/jardcs/v12sp1/20201088
Kolla, S., Sk, A., Veeramachaneni, S., & Sk, N. M. (2022). Logic Locking Designs at Transistor Level for Full Adders. 2022 IEEE International Symposium on Smart Electronic Systems (iSES), 289–292. https://doi.org/10.1109/iSES54909.2022.00065
Krishna, M. Y. S., Arya, A., Ansari, S., Awasya, S., Sushakar, J., & Uikey, N. (2023). Real Time Door Unlocking System using Facial Biometrics based on IoT and Python. 2023 IEEE International Students’ Conference on Electrical, Electronics and Computer Science (SCEECS), 1–5. https://doi.org/10.1109/SCEECS57921.2023.10063142
Lee, J. Y., & Lee, J. (2021). Current Research Trends in IoT Security: A Systematic Mapping Study. Mobile Information Systems, 2021(1), 8847099. https://doi.org/10.1155/2021/8847099
Lojda, J., Panek, R., Podivinsky, J., Cekan, O., Krcma, M., & Kotasek, Z. (2021). Testing Embedded Software Through Fault Injection: Case Study on Smart Lock. 2021 IEEE 22nd Latin American Test Symposium (LATS), 1–6. https://doi.org/10.1109/LATS53581.2021.9651770
Mahendra, S., Sathiyanarayanan, M., & Vasu, R. B. (2018). Smart Security System for Businesses using Internet of Things (IoT). 2018 Second International Conference on Green Computing and Internet of Things (ICGCIoT), 424–429. https://doi.org/10.1109/ICGCIoT.2018.8753101
Morales-Nava, R., Sosa Sales, A., Jiménez-Echeverría, J. R., Enríquez Díaz, J. M., & Barreto De La Cruz, J. L. (2023). Implementación de un control de acceso en cerradura eléctrica con base al reconocimiento facial y huella dactilar para elevar el nivel de seguridad en los hogares. Ciencia Latina Revista Científica Multidisciplinar, 7(3), 5976–5991. https://doi.org/10.37811/cl_rcm.v7i3.6602
Nagasree Y, L. V., Rupa, Ch., Dharmika, B., Nithin, T. G., & Vineela, N. (2021). Intelligent Secure Smart Locking System using Face Biometrics. 2021 International Conference on Recent Trends on Electronics, Information, Communication & Technology (RTEICT), 268–273. https://doi.org/10.1109/RTEICT52294.2021.9573869
Padhan, D. G., Varma, S. N., C, V., Divya, M., Manasa, S., & Pakkiraiah, B. (2023). Home Security System Based on Facial Recognition. 2023 IEEE 3rd International Conference on Sustainable Energy and Future Electric Transportation (SEFET), 1–6. https://doi.org/10.1109/SeFeT57834.2023.10244798
Panarello, A., Tapas, N., Merlino, G., Longo, F., & Puliafito, A. (2018). Blockchain and IoT Integration: A Systematic Survey. Sensors, 18(8). https://doi.org/10.3390/s18082575
PBV, R. R., Sonaleo Mandapati, V., Pilli, S. L., Lahari Manojna, P., Chandana, T. H., & Hemalatha, V. (2024). Home Security with IOT and ESP32 Cam—AI Thinker Module. 2024 International Conference on Cognitive Robotics and Intelligent Systems (ICC - ROBINS), 710–714. https://doi.org/10.1109/ICC-ROBINS60238.2024.10533960
Praneeth, D., Rekha Sree, T., Viswanatha, V., & Abhiram Sai, M. (2024). AI Enabled Home Security System Using Object Detection and Face Recognition with Haar Cascade Algorithm. 2024 International Conference on Recent Advances in Science and Engineering Technology (ICRASET), 1–6. https://doi.org/10.1109/ICRASET63057.2024.10895751
Quiñones, M. F., Pachar Bravo, H. P., Martínez-Curipoma, J., Quiñones, L., & Torres, R. (2020). Developing and evaluation of an IoT mobile gateway for 4G LTE networks. Enfoque UTE, 11(4), 16–26. https://doi.org/10.29019/enfoqueute.v11n4.634
R. S, N., Venkatasamy, R., Dhanraj, J. A., Aravinth, S., Balachandar, K., & N, Dhamodharan. (2022). Design and Development of IOT based Smart Door Lock System. 2022 Third International Conference on Intelligent Computing Instrumentation and Control Technologies (ICICICT), 1525–1528. https://doi.org/10.1109/ICICICT54557.2022.9917767
Shreya, K., Divakarla, L. P., Kumar, K. J., & Vishwas, H. N. (2024). Fortifying Digital Security: A Machine Learning and Explainable AI Framework for Password Strength Assessment. 2024 8th International Conference on Electronics, Communication and Aerospace Technology (ICECA), 1358–1364. https://doi.org/10.1109/ICECA63461.2024.10800823
Tiwari, S., Thakur, S., Shetty, D., & Pandey, A. (2018). Smart Security: Remotely Controllable Doorlock. 2018 Second International Conference on Inventive Communication and Computational Technologies (ICICCT), 979–984. https://doi.org/10.1109/ICICCT.2018.8473161
Uddin, K. M. M., Shahela, S. A., Rahman, N., Mostafiz, R., & Rahman, M. M. (2022). Smart Home Security Using Facial Authentication and Mobile Application. International Journal of Wireless and Microwave Technologies (IJWMT), 12(2), 40–50. https://doi.org/10.5815/ijwmt.2022.02.04
Vaishnavi, T., N, N., Archana, T., Murali Kishanlal, M. S., Jayasankar, S., & Rahul, D. (2025). Hybrid Unified AI-Based Biometric Authentication: A Low-Power, High-Security Scheme. 2025 International Conference on Emerging Smart Computing and Informatics (ESCI), 1–6. https://doi.org/10.1109/ESCI63694.2025.10987946
Vaishnavi, T., Rekha, N, N., M, D., Giri, P., & Kanan, M. (2024). Unified AI-Based Biometric Authentication: A Low-Power, High-Security Solution. 2024 International Conference on Innovative Computing, Intelligent Communication and Smart Electrical Systems (ICSES), 1–8. https://doi.org/10.1109/ICSES63760.2024.10910877
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2025 Dick Díaz-Delgado, Sergio M. Vigil-Ramírez, Luis J. Acho-Cachay, Brandom R. Tuanama-Chávez, Luis A. Rojas-Puerta

This work is licensed under a Creative Commons Attribution 4.0 International License.
The authors retain their rights:
a. The authors retain their trademark and patent rights, as well as any process or procedure described in the article.
b. The authors retain the right to share, copy, distribute, execute and publicly communicate the article published in the Revista Científica de Sistemas e Informática (RCSI) (for example, place it in an institutional repository or publish it in a book), with an acknowledgment of its initial publication in the RCSI.
c. Authors retain the right to make a subsequent publication of their work, to use the article or any part of it (for example: a compilation of their works, notes for conferences, thesis, or for a book), provided that they indicate the source of publication (authors of the work, journal, volume, number and date).








